SMS Phishing Detection and Prevention System
SMS Phishing Security
Ryota Iwai, Shou Harada and Yosuke Kubo
Core Network Development Department
Abstract
Phishing attacks in which users are tricked into accessing a fake website via an SMS so that information can be stolen have been increasing in recent years. The attacking techniques are becoming more diverse and sophisticated, and it is no longer easy for the recipient to recognize a phishing SMS. NTT DOCOMO has therefore developed a system that determines whether an SMS message is a phishing SMS before the user receives it, and if it is a phishing SMS, discards it before it is sent to the user, thereby preventing harm. This article provides an overview of the technologies behind this system.
-
01.Introduction
Phishing attacks that use a Short Message Service (SMS) ...
Open

Phishing attacks that use a Short Message Service (SMS)*1 have been increasing in recent years. Such attacks involve sending SMS messages purporting to be from well-known companies or services that actually exist (hereafter referred to as “phishing SMS”) to users to trick them into accessing a fake website so that their personal or credit card information can be stolen, or so that malware is downloaded to their devices. The techniques used to lure users to fake websites are becoming more sophisticated, and in some cases, it is extremely difficult to distinguish between a legitimate site and phishing site just by looking at the text or the website. Such messages may look like a missed delivery notice from a courier company or a notice of unpaid cell phone bills, and the scale of the harm they cause is increasing. To address this issue, NTT DOCOMO has developed an SMS phishing detection and prevention system that automatically determines whether an SMS message is a phishing SMS before it is received, and if it is, discards it on the DOCOMO network before it is sent to the user, thereby preventing harm. This article describes an overview of the technologies behind this system.
- SMS: A service for sending/receiving short text-based messages mainly between mobile terminals.
-
02.Architecture of SMS Phishing Detection and Prevention System
2.1 Network Configuration
Open

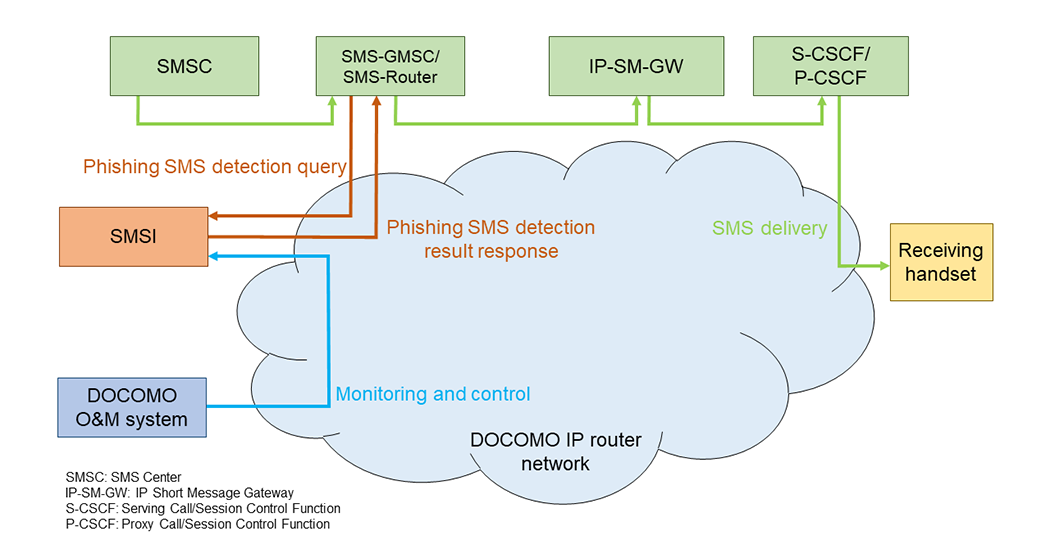
The overall network configuration is shown in Figure 1. NTT DOCOMO has built a new SMS Inspector (SMSI)*2 system, which has its own phishing SMS database and is equipped with functions to determine whether a message is a phishing SMS. In addition, we added a new interface to SMS-Gateway Mobile Switching Center (SMS-GMSC)/SMS-Router*3, which is responsible for relaying, storing, and distributing SMS, to connect with SMSI and link it with the conventional network infrastructure for SMS processing. SMS-GMSC/SMS-Router connects to SMSI via the DOCOMO IP router network, a dedicated network connecting DOCOMO locations nationwide. The DOCOMO Operation & Maintenance (O&M) system, which monitors NTT DOCOMO facilities nationwide, and SMSI are also connected via the DOCOMO IP router network to monitor, operate and control equipment.
2.2 Basic Control Method
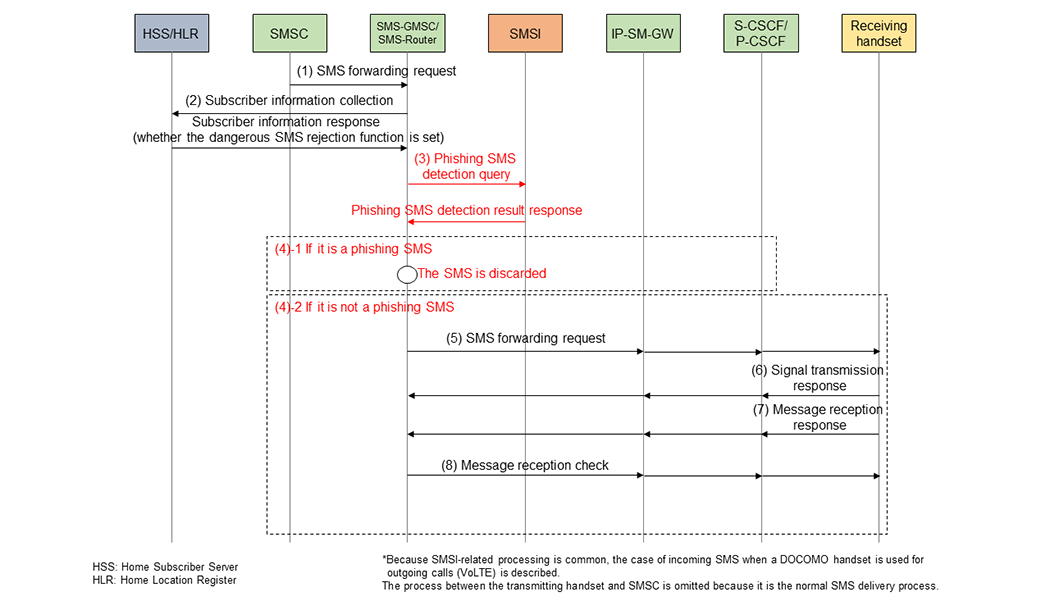
The processing sequence related to SMS control, which includes anti-phishing SMS function processing, is shown in Figure 2. In addition to the processes specified in SMS standards [1], a new process for judging and discarding phishing SMS is added. These processes are implemented in the basic control method. First, before sending an SMS to a user, the SMS-GMSC/SMS-Router consults subscriber information to check whether a dangerous SMS rejection function is set by the user (Fig. 2(2)). Confirmation of the setting status of this function is implemented with existing functions for collecting/responding to subscriber information. Processing time is almost the same as for sending existing SMS. If the dangerous SMS rejection function is enabled, a phishing SMS detection query message is created and sent to the SMSI using the header and body information contained in the SMS (Fig. 2(3)). Note that the SMS-GMSC/SMS-Router does not send the SMS itself to SMSI but generates and sends a request message to determine if it is a phishing SMS by protocol conversion of the SMS message. SMSI executes the phishing SMS judgment process using its own database for phishing SMS detection query messages from each SMS-GMSC/SMS-Router installed nationwide and sends the judgment result of whether the message is a phishing SMS as a phishing SMS detection result response message to the SMS-GMSC/SMS-Router that made the query. When the SMS-GMSC/SMS-Router receives a phishing SMS detection result response message, it discards the SMS if it is a phishing SMS (Fig. 2(4)-1). If not, it executes delivery based on the conventional SMS control process (Fig. 2(4)-2). The SMS-GMSC/SMS-Router implements a processing function for SMSI access failure so that SMS delivery will not be disabled in the event of SMSI abnormal operation. If there is no response from the SMSI, or if the content of the phishing SMS detection result response message from the SMSI is not appropriate, this function notifies a maintenance operator, temporarily stops sending phishing SMS detection query messages, and carries out SMS delivery as before. Furthermore, the SMS-GMSC/SMS-Router is equipped with a function that allows it to omit querying the SMSI for SMSs defined as reliable SMS messages at the SMS-GMSC/SMS-Router side. In determining whether a message is a trustworthy SMS message, a variety of decision logic is combined with multiple SMS parameters to enable detailed control and reduce the load on SMSI by more than 50%, thereby speeding up and reducing the load on SMSI decision processing.
2.3 Phishing SMS Decision Process Update Method
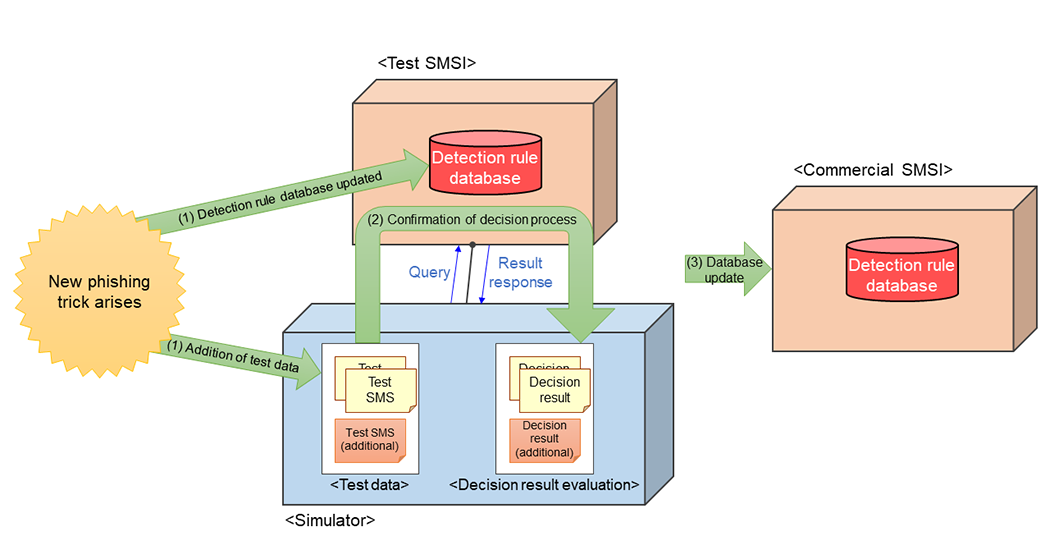
SMSI maintains its own database of phishing SMSs and uses multiple determination methods to determine whether each SMS is a phishing SMS. Although the database contains a large amount of data and is compatible with all types of phishing SMS, phishing tactics are constantly changing and incorporating social trends, etc., and continue to diversify and become more sophisticated. Therefore, the database needs to be updated accordingly. However, if the data is incorrect, it may cause issues such as phishing SMSs being overlooked, so it is necessary to verify the validity of the data before updating the database. Therefore, NTT DOCOMO maintains methods to evaluate the validity of new phishing SMS information collected from multiple channels before reflecting it in the database. The evaluation method for new phishing SMS information is shown in Figure 3. Based on the phishing SMS information collected from multiple channels (e.g., phishing SMS itself and URL information of phishing sites), the detection rule database of a test SMSI and the test data of a simulator are updated simultaneously (Fig. 3(1)). The simulator has functions to create and send phishing SMS detection query messages from SMS-GMSC/SMS-Router to SMSI, and to evaluate whether phishing SMS detection result response messages from SMSI are as expected. The updated test data is processed through the test SMSI, and the simulator evaluates the decision process for existing and added phishing SMSs (Fig. 3(2)). If the appropriate results are obtained, they are reflected in the database of the commercial SMSI that makes decisions for actual user SMSs (Fig. 3(3)). NTT DOCOMO has developed and built its own dedicated system to automate this evaluation, which enables testing to be conducted with a minimum of man-hours and time, thus making it possible to respond quickly when new phishing tricks arise.
- SMSI: A system that performs phishing SMS determination processing using a proprietary database.
- SMS-GMSC/SMS-Router: A device between the SMS center server and the local exchange of the SMS sending/receiving user that is responsible for routing signals.
-
03.Conclusion
This article provided an overview of the technologies ...
Open

This article provided an overview of the technologies behind an SMS phishing detection and prevention system that can identify phishing SMSs on a network and discard them. Jointly with the information and telecommunications industry, government agencies, financial institutions and other organizations, NTT DOCOMO regularly holds workshops on smishing*4 measures to reduce the number of SMS phishing victims and works on society-wide anti-SMS phishing measures. We will continue to implement countermeasures for SMS phishing by linking with technologies related to the collection of new phishing SMS information, advancing technologies to countermeasure new phishing modus operandi, and strengthening the accuracy of phishing SMS detection, etc.
- Smishing: SMS-based phishing scams.
-
REFERENCES
Open

- [1] 3GPP TS23.040 V17.1.0: “Technical realization of the Short Message Service (SMS),” Jun. 2021.